Source: RSA RESEARCH TERRACOTTA VPN Enabler of Advanced Threat Anonymity
EXECUTIVE SUMMARY
In this report, RSA Research explores in depth a
malware-supported VPN network, known internally to RSA as Terracotta.
Terracotta is an active launch-platform for APT activities of Shell_Crew /
DeepPanda and other APT actors, used to obscure the origins of the threat
actors’ malicious activities. It is ensnaring a new class of victims
(legitimate commercial and government entities, unknowinly serving VPN nodes
and bandwith) into larger-scale APT cases. Fortunately, enlistment in the Terracotta
network is readily preventable by using well-established cybersecurity
practices. Detection and mitigation for enlisted systems is also quite
feasible. Terracotta is commercially marketed in the People’s Republic of China
(PRC) under several different brand names. VPN services are quite marketable in
China as a means to anonymously traverse government internet censorship.
Terracotta’s malicious methods for acquiring nodes and theft of bandwidth
likely derives substantial cost-savings for its operators. Having provided
Terracotta VPN indicators to trusted partners, RSA has received multiple
reports of (and since observed) suspected nation-state sponsored campaign
activity originating from Terracotta VPN IP addresses. Targets appear to have
included Western governments and several commercial entities. By using
Terracotta VPN, advanced threat actors appear to originate from seemingly
benign sources. Blocking, restricting, or detecting by IP address indicators is
difficult because new nodes (hosted in legitimate organizations) are being
continuously added. This report by RSA Research may represent the first
exposure of a PRC-based VPN operation that maliciously, efficiently and rapidly
enlists vulnerable servers around the world. It is the first time RSA Research
has seen Shell_Crew / DeepPanda and other similar APT actors using such
networks for anonymization and obfuscation.
BACKGROUND
Virtual Private Networks (VPN) are very popular. They are
part and parcel for almost every enterprise network, especially those with
remote employees. Aside from VPNs for enterprises, there are many reputable
commercial VPN services that offer low-cost, reliable service to individual
users. These users employ VPNs for reasons that might include connection
security, protection of private data, online gaming acceleration, and bypassing
service provider restrictions. VPNs are also used by cyber criminals, as it
allows them to obscure their true source location. When a commercial VPN
service provider uses resources such as servers and copious bandwidth stolen or
repurposed from unsuspecting victims for purposes of profit, analysis and
reporting are in order. In this report, RSA Research exposes one such operator
doing business with multiple VPN brand names marketed primarily in the People’s
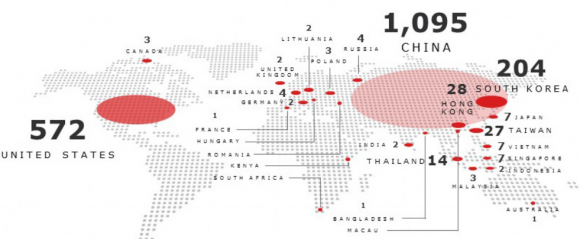
Republic of China (PRC). Operating with more than 1500 end nodes around the
world, RSA Research has confirmed that at least thirty of the host systems are
compromised Windows servers that were “harvested” without the victims’
knowledge or permission. The operators behind Terracotta VPN continue their
broad campaign to compromise multiple victim organizations around the world.
RSA Research is reporting on the associated VPN operator
because:
• There is evidence of compromise of multiple victim
organization systems around the world,
• There is evidence of illicit installation of software
and malicious remote access tools on the victims’ servers, and
• There is evidence of theft of victims’ resources and
bandwidth to serve clients (including advanced threat actors) with a
high-performance anonymity service.